AuthorPeter Oakes is an experienced anti-financial crime, fintech and board director professional. Archives
January 2025
Categories
All
|
Back to Blog
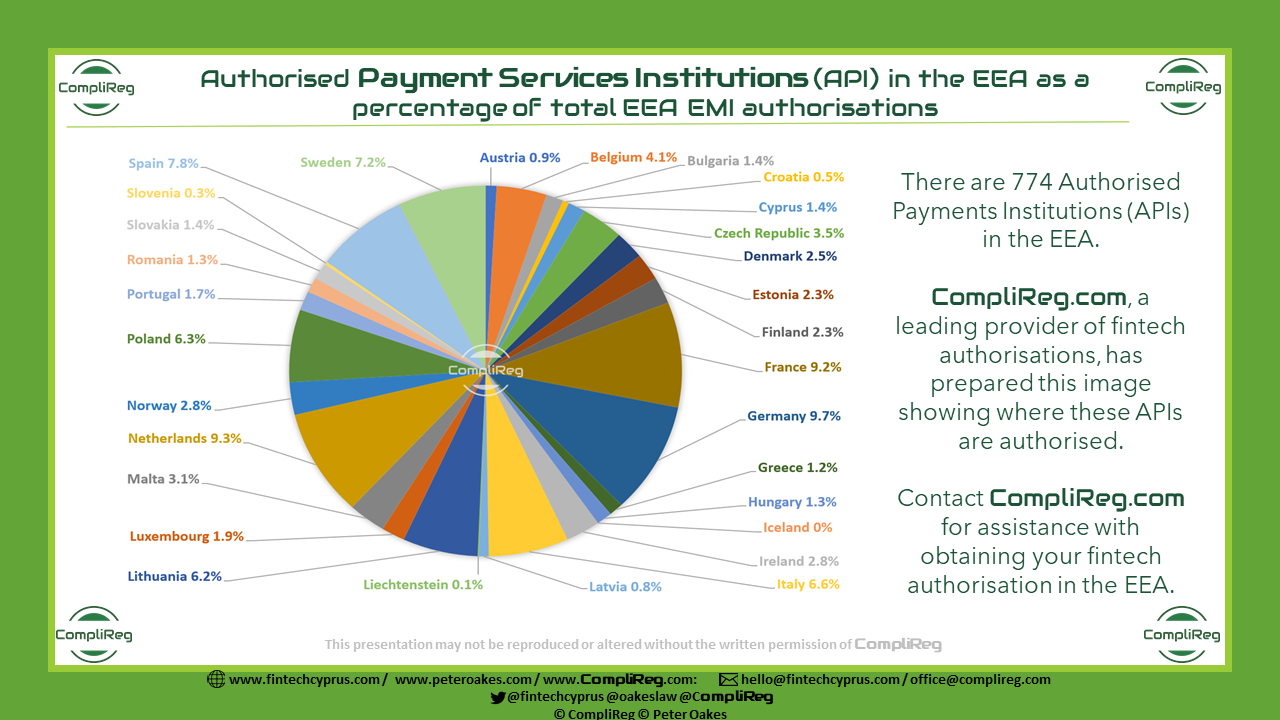
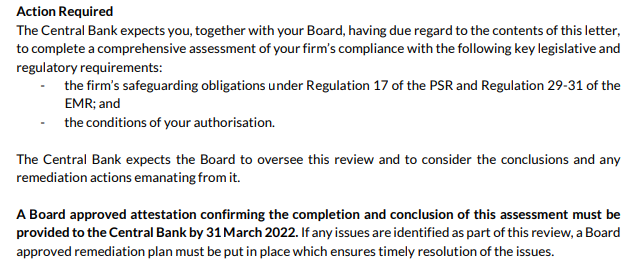
Key Findings of Cyprus National Risk Assessment with respect to Virtual Assets and Virtual Asset Service Providers (November 2021)Key Findings:
Recommended Actions:
0 Comments
Read More
Back to Blog
UK Registered Cryptoasset Map Version 1.0 |
© CompliReg.com Dublin 2, Ireland ph +353 1 639 2971
| www.complireg.com | officeATcomplireg.com [replace AT with @]
| www.complireg.com | officeATcomplireg.com [replace AT with @]